SSO with Microsoft Azure Active Directory
Customer configuration with Azure
1. Open portal.azure.com
2. Go to the Azure Active Directory > Enterprise applications > + New Application
3. Now click on “+ Create your application”
4. Under app name, type "Product Fruits Saml”
5. Under “What are you looking to do with your application?” select “Integrate any other application you don’t find in the gallery (Non-gallery)” and click Create

6. Click “Single sign-on” in the left pane and then under “Select a single sign-on" method select "SAML”. In the “1. Basic SAML Configuration” box, click “Edit”
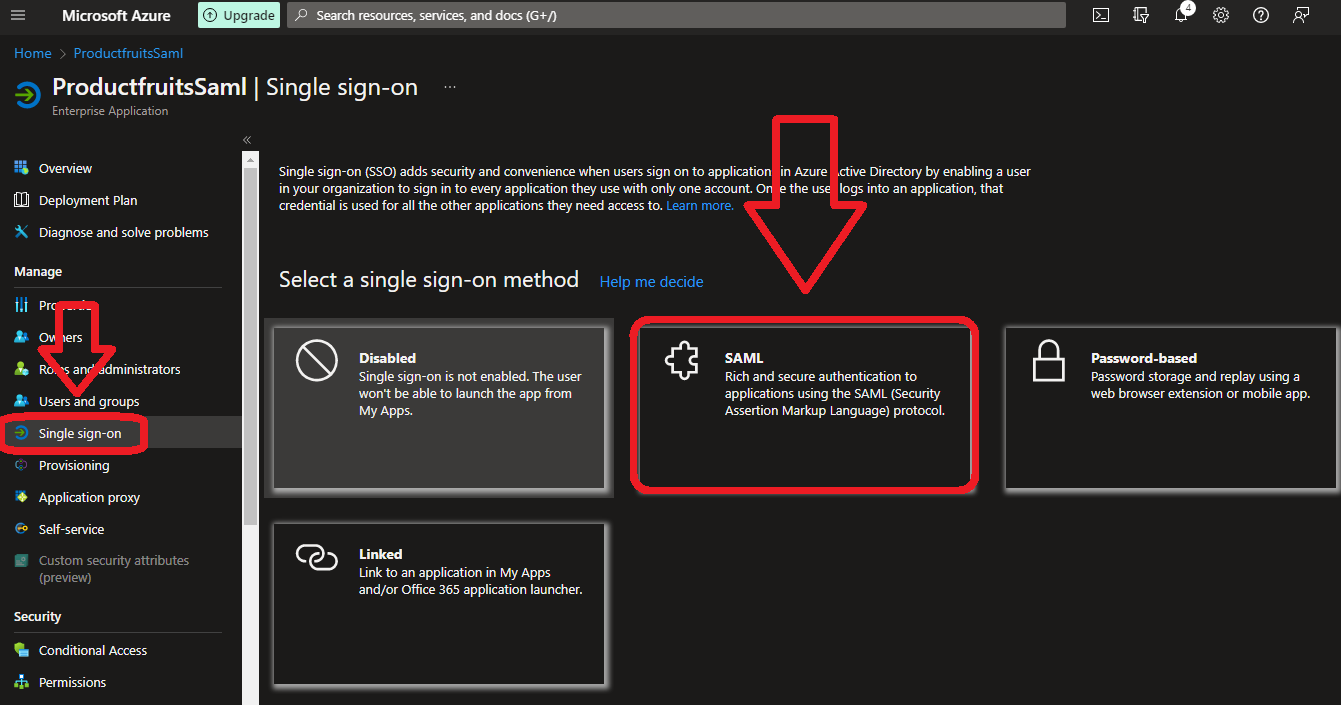
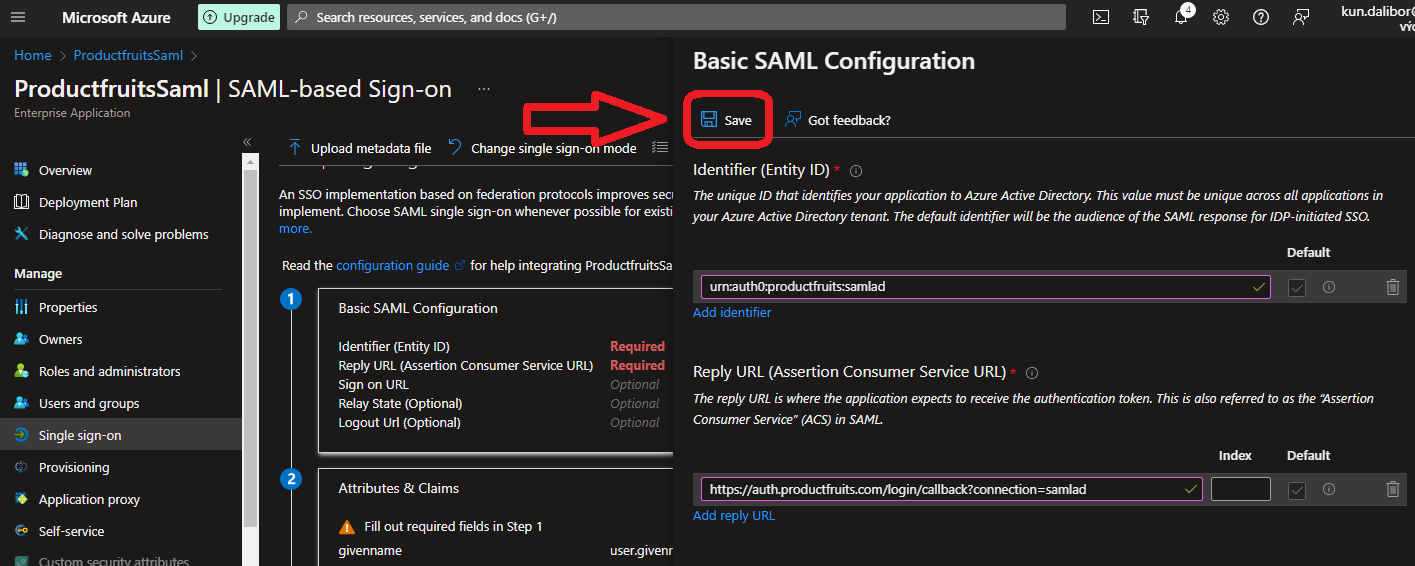
7. Under Identifier (EntityId) set up the identifier as shown in the following example: urn:auth0:productfruits:COMPANY_SSO_IDENTIFIER
(You can find Product Fruits COMPANY_SSO_IDENTIFIER under the user management SSO tab)
8. Set the Reply URL (Assertion Consumer Service URL) to
https://auth.productfruits.com/login/callback?connection=COMPANY_SSO_IDENTIFIER9. Click “Save”
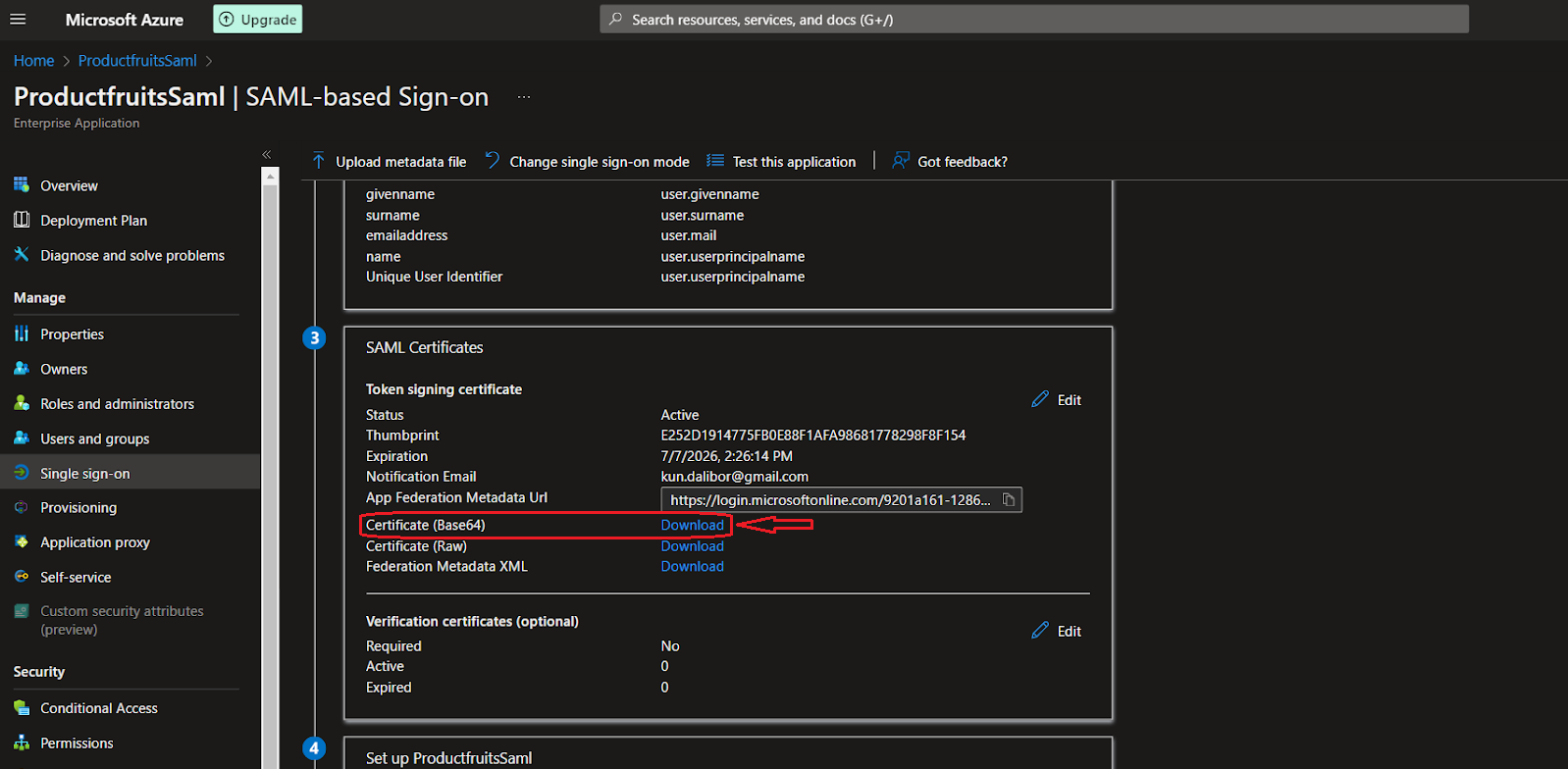
10. In the “3. SAML Signing Certificate” box, click “Download” next to “Certificate (Base64)”
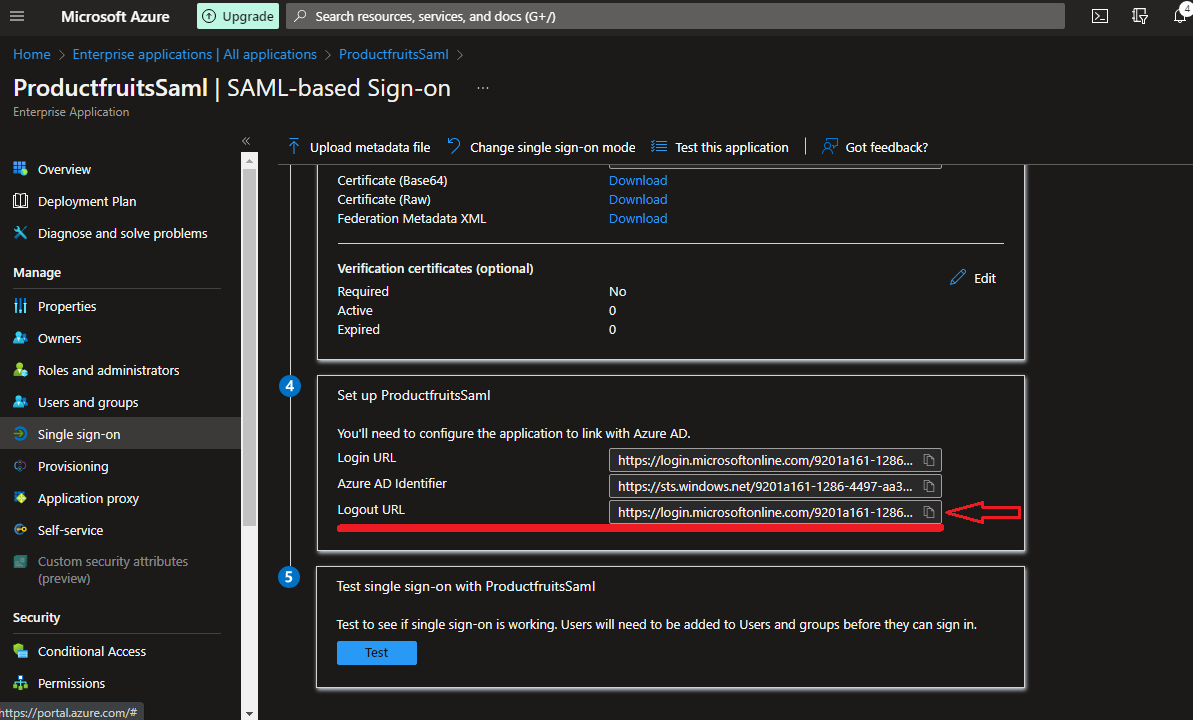
11. In the “4. Set up the AzureViaSaml” box, copy the Login URL. It will look something like:
https://login.microsoftonline.com/xxx/saml2 12. Optionally, copy the Logout URL.
Note:
Once we set up SSO for a particular domain the Product Fruits login will automatically redirect all requests to the identity provider side. Make sure you have already set up everything on the Azure side and that all values are valid.
