SSO with OneLogin
What we need before beginning
- A SAML 2.0 Endpoint URL (Step 5 in customer configuration below)
- An SLO Endpoint URL (Step 5 in customer configuration below)
- A Certificate (Step 7 in customer configuration below)
- An email Domain(s)
Customer configuration with OneLogin
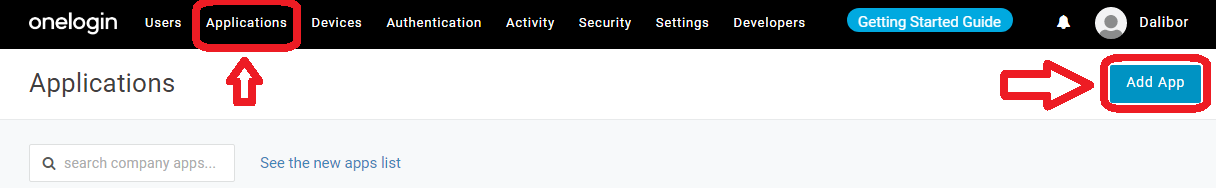
1. Log in to the OneLogin Dashboard, and click Applications > Add App.
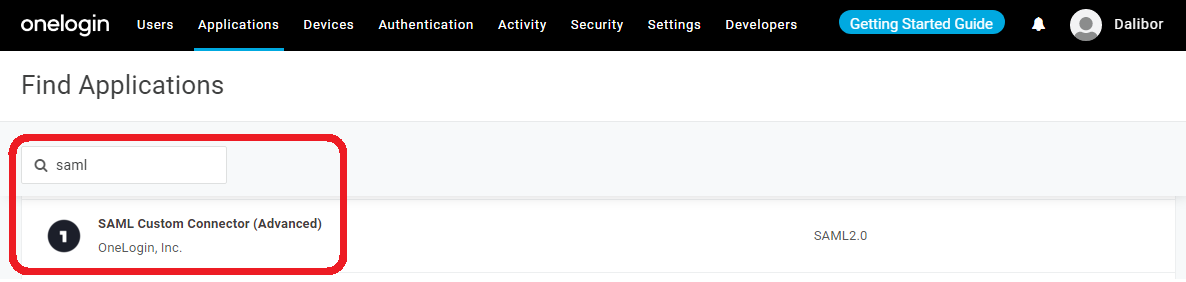
2. Search for SAML (SAML Custom Connector (Advanced))
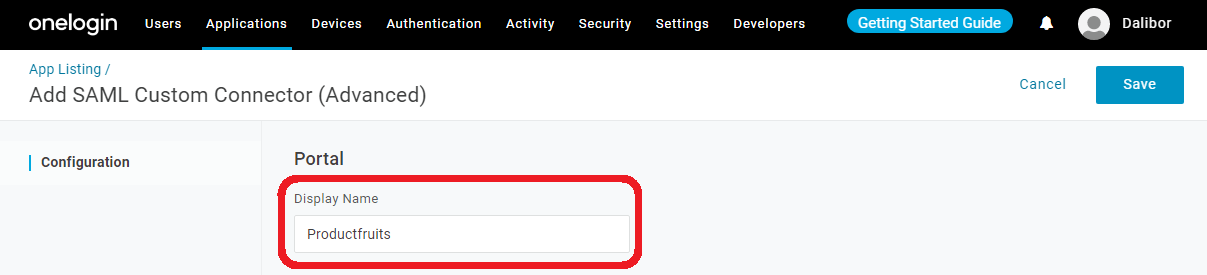
3. Change the Display Name to “Product Fruits” (This name will be displayed on the OneLogin login screen)
4. Click SAVE.
5. Go to the SSO tab and copy the values for the SAML 2.0 Endpoint (HTTP) and SLO Endpoint (HTTP)
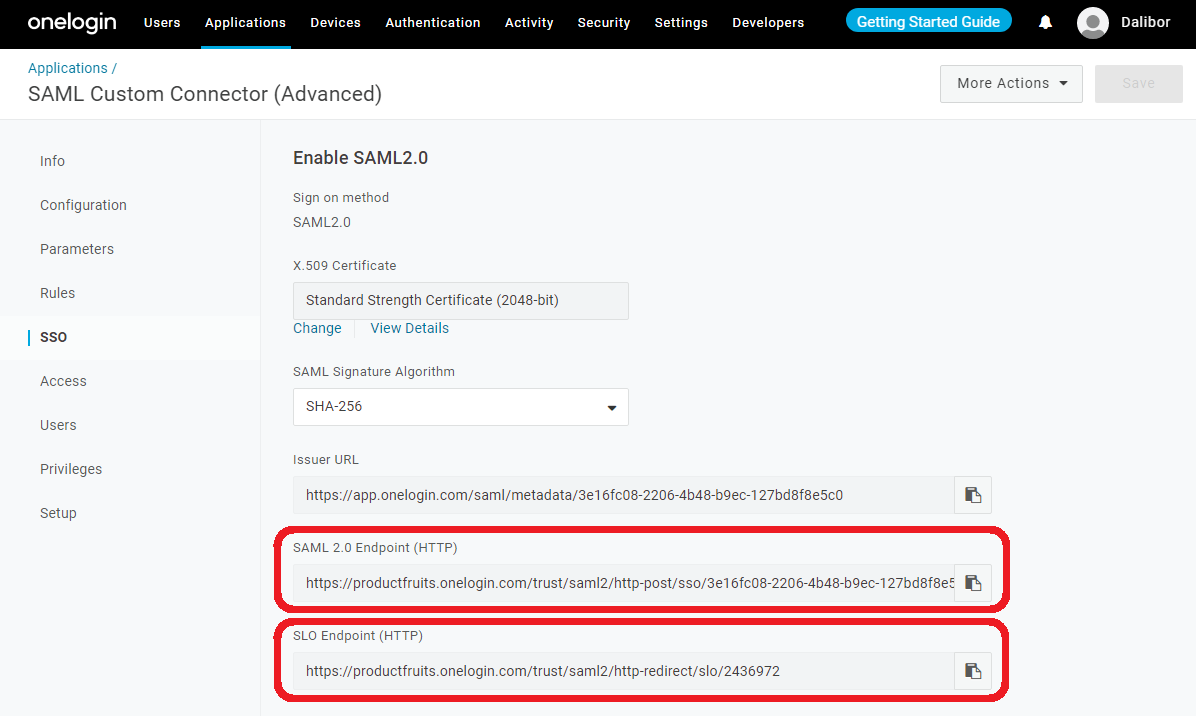
6. Click SAVE.
7. Click on the View Details link in the X.509 Certificate field.
8. Download the X.509 certificate.
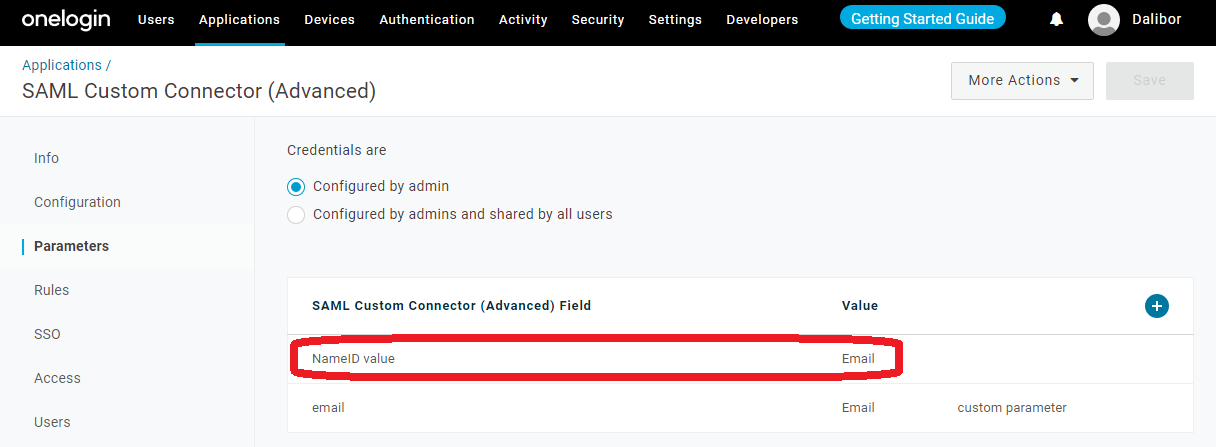
9. Go to the Parameters tab and map “email” to the NameId and Email (Product Fruits uses the email claim to identify the user)
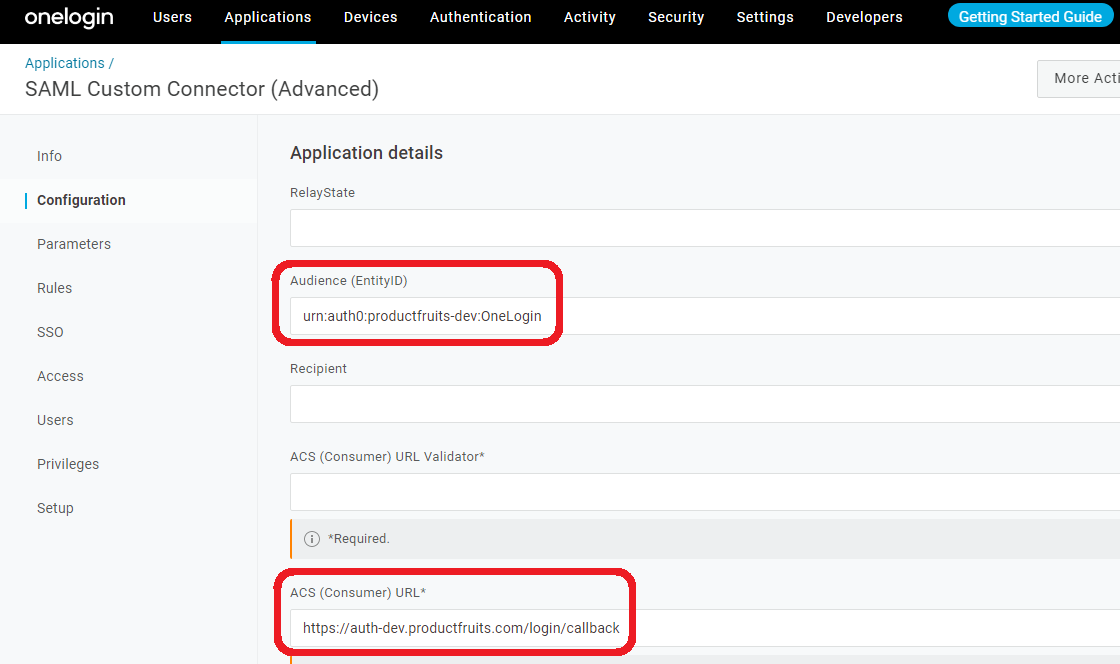
10. Go to the Configuration tab and setup the Audience (EntityID) and ACS (Consumer) URLs as follows:
ACS (Consumer) URL:
https://auth.productfruits.com/login/callback?connection=COMPANY_SSO_IDENTIFIER Audience (EntityID): urn:auth0:productfruits: COMPANY_SSO_IDENTIFIER
(You can find Product Fruits COMPANY_SSO_IDENTIFIER under the user management SSO tab)
Note: Once we set up SSO for a particular domain the Product Fruits login will automatically redirect all requests to the identity provider side. Make sure you have already set up everything on the OneLogin side and that all values are valid.